Korean-led consortium begins construction at 350MW solar PV plant in Texas



Demand for electricity is up in the United States, and so is its price. One way to increase supply and lower costs is to build new power plants, but that can take years and cost a fortune. Talgat Kopzhanov is working on a faster, more affordable solution: the generator replacement interconnection process.
The technique links renewable energy sources to the grid connections of shuttered or underutilized power facilities and coal plants. The process uses the existing interconnection rights and infrastructure when generating electricity, eliminating the years-long approval process for constructing new U.S. power facilities.
Employer
Middle River Power, in Chicago
Job title
Asset manager
Member grade
Senior member
Alma maters
Purdue University in West Lafayette, Ind., and Indiana University in Bloomington
Kopzhanov, an IEEE senior member, is an asset manager for Middle River Power, based in Chicago. The private equity–sponsored investment and asset management organization specializes in U.S. power generation assets.
“Every power plant has its own interconnection rights,” he says, “but, amazingly, most are not fully utilizing them.” Interconnection rights give a new power source—such as solar energy—permission to connect to a high-voltage transmission system.
“We build the new renewable energy resources on top of them,” Kopzhanov says. “It’s like colocating a new power plant.”
He recently oversaw the installation of two generator-replacement interconnection projects, one for a solar system in Minnesota and the other for a battery storage facility in California.
Artificial intelligence data centers are driving up demand and raising electricity bills globally. Although tech companies and investors are willing to spend trillions of U.S. dollars constructing new power facilities, it can take up to seven years just to secure the grid interconnection rights needed to start building a plant, Kopzhanov says. The lengthy process involves system planning, permit requests, and regulatory approvals. Only about 5 percent of new projects are approved each year, he says, in part because of grid reliability issues.
The interconnection technique takes about half the time, he says, bringing cleaner energy online faster. By overcoming interconnection bottlenecks, such as major transmission upgrades that delay renewable projects, the process speeds up project timelines and lowers expenses.
If you want to work in a secure, recession-proof industry, consider a career in power engineering, Kopzhanov says—especially in an unstable job market, when even Amazon, Microsoft, and other large companies are laying off thousands of engineers.
The power industry desperately needs engineers. The global power sector will require between 450,000 and 1.5 million more engineers by 2030 to build, implement, and operate energy infrastructure, according to an IEEE Spectrum article based on a study conducted this year of the power engineering workforce by the IEEE Power & Energy Society.
One of the reasons for the shortage, Kopzhanov says, is that the power sector doesn’t seem exciting to young engineers.
“It has not been popular because the technologies we’re implementing nowadays were invented quite a long time ago,” he says. “So there were not too many recent innovations.”
But with new technologies being introduced, such as the generator replacement interconnection process, now is a great time to get into the industry, he says.
“We are facing lots of different kinds of interesting and big challenges, and we definitely need power engineers who can solve them, such as the supply and demand situation facing us,” he says. “We need right-minded people who can deal with that.
“Until this point, the marvelous engineering systems that have been designed and built with close to 100-percent reliability are not going to be the case moving forward, so we have to come up with innovative approaches.”
Just because you have a power engineering degree, however, doesn’t mean you have to work as a power engineer, he says.
“Most students might assume they will have to dedicate themselves to only being a power engineer for the rest of their life—which is not the case,” he says. “You can be on the business side or be an asset manager like me.
“The power sector is an extremely dynamic and vast area. You’ll have many paths to pursue along your career journey.”
Kopzhanov explains the technique in an on-demand educational webinar, Unlocking Surplus Interconnection Service. Colocating Renewable and Thermal Power Plants, hosted by the IEEE Power & Energy Society. The webinar is available to the public for a fee.
Kopzhanov has been involved with several recent generator replacement interconnection installations. In May a large-scale solar project in Minnesota replaced a retiring coal plant with approximately 720 megawatts of solar-powered generators, making it the largest solar-generating facility in the region. The first 460 MW of capacity is expected to be operational soon.
Another new installation, developed with Middle River, is a portfolio of battery storage projects colocated with natural gas facilities in California. It used existing and incremental interconnection capacity to add the storage system. The surplus renewable energy from the batteries will be used during peak times to reduce the plant’s greenhouse gas emissions, according to a Silicon Valley Clean Energy article about the installation.
“These projects are uniquely positioned to be colocated with existing power plants,” Kopzhanov says. “But, at the same time, they are renewable and sustainable sources of power—which is also helping to decarbonize the environment and meet the emission-reduction goals of the state.”
Born and raised in Taraz, Kazakhstan, Kopzhanov was surrounded by relatives who worked in the power industry. It’s not surprising that he has pursued a career in the field.
Until 1991, when the country was still a Soviet republic, most Kazakhs were required to help build the country’s power and transmission systems, he says. His mother and father are chemical engineers, and his grandfather was involved in the power industry. They told him about how they designed the transformers and overhead power lines. From a young age, he knew he wanted to be an engineer too, he says.
Today the Central Asian country is a major producer of oil, gas, and coal.
Kopzhanov left Kazakhstan in 2008 to pursue a bachelor’s degree in electrical engineering at Purdue University, in West Lafayette, Ind.
After graduating in 2012, he was hired as an electrical design engineer by Fluor Corp. in Farnborough, England. He oversaw the development of a master plan for a power project there. He also engineered and designed high-voltage switchgears, substations, and transformers.
“Every power plant has its own interconnection rights but, amazingly, most are not fully utilizing them.”
In 2015 he joined ExxonMobil in Houston, working as a project manager. During his six years there, he held managerial positions. Eventually, he was promoted to asset advisor and was responsible for evaluating the feasibility of investing in decarbonization and electrification projects by identifying their risks and opportunities.
He decided he wanted to learn more about the business aspects of running a company, so he left in 2021 to pursue an MBA at Indiana University’s Kelley School of Business, in Bloomington. During his MBA program, he briefly worked as a consultant for a lithium-ion manufacturing firm, offering advice on the viability of their proposed projects and investments.
“Engineers aren’t typically connected to the business world,” he says, “but having an understanding of what the needs are and tailoring your future goals toward that is extremely important. In my view, that’s how you’ll become a great technical expert. I definitely recommend that engineers have some kind of understanding of the business side.”
He joined Middle River shortly after graduating from Indiana with his MBA in 2023.
Kopzhanov was introduced to IEEE by a colleague at ExxonMobil after he asked the member about an IEEE plaque displayed on his desk. The coworker explained the activities he was involved in, as well as the process for joining. Kopzhanov became a member in 2019, left, and then rejoined in 2023.
“That was one of the best decisions I have made,” he says.
A member of the IEEE Power & Energy Society, he says its publications, webinars, conferences, and networking events keep him current on new developments.
“Being able to follow what’s happening in the industry, especially in the space where you’re working, is something that has benefited me a lot,” he says.
He has helped organize conferences and reviews research papers.
“It’s those little things that have a significant impact,” he says. “Volunteering is a key piece of belonging to IEEE.”
This article was updated on 13 January 2026.


Cyber incidents haven’t ceased to escalate in 2025, and they keep making their presence felt more and more impactfully as we transition into 2026. The quick evolution of novel cyber threat trends leaves data centers increasingly exposed to disruptions extending beyond the traditional IT boundaries.
The Uptime Institute’s annual outage analysis shows that in 2024, cyber-related disruptions occurred at roughly twice the average rate seen over the previous four years. This trend aligns with findings from Honeywell’s 2025 Cyber Threat Report, which identified a sharp increase in ransomware and extortion activity targeting operational technology environments based on large-scale system data.
There are many discussions today around infrastructure complexity and attack sophistication, but it’s a lesser-known reality that human error in cybersecurity remains a central factor behind many of these incidents. Routine configuration changes, access decisions, or decisions taken under stress can create conditions that allow errors to sneak in. Looking at high-availability environments, human error often becomes the point at which otherwise contained threats begin to escalate into bigger problems.
As cyberattacks on data centers continue to grow in number, downtime is carrying heavier and heavier financial and reputational consequences. Addressing human error in cybersecurity means recognizing that human behavior plays a direct role in how a security architecture performs in practice. Let’s take a closer look.
How Attackers Take Advantage of Human Error in Cybersecurity
Cyberattacks often exploit vulnerabilities that stem from both superficial, maybe even preventable mistakes, as well as deeper, systemic issues. Human error in cybersecurity often arises when established procedures are not followed through consistently, which can create gaps that attackers are more than eager to exploit. A delayed firmware update or not completing maintenance tasks can leave infrastructure exposed, even when the risks are already known. And even if organizations have defined policies to reduce these exposures, noncompliance or insufficient follow-through often weakens their effectiveness.
In many environments, operators are aware that parts of their IT and operational technology infrastructure carry known weaknesses, but due to a lack of time or oversight, they fail to address them consistently. Limited training also adds to the problem, especially when employees are expected to recognize and respond to social engineering techniques. Phishing, impersonation, and ransomware attacks are increasingly targeting organizations with complex supply chains and third-party dependencies, and in these situations, human error often enables the initial breach, after which attackers move laterally through systems, using minor mistakes to trigger disruptions.
Why Following Procedures is Crucial
Having policies in place doesn’t always guarantee that the follow-through will be consistent. In everyday operations, teams often have to juggle many things at once: updates, alerts, and routine maintenance, and small steps can be missed unintentionally. Even experienced staff can make these kinds of mistakes, especially when managing large or complex environments over an extended period of time. Gradually, these small oversights can add up and leave systems exposed.
Account management works similarly. Password rules, or the policies for the handling of inactive accounts are usually well-defined; however, they are not always applied homogeneously. Dormant accounts may go unnoticed, and teams can fall behind on updates or escape regular review. Human error in cybersecurity often develops step by step through workloads, familiarity, and everyday stress, and not because of a lack of skill or awareness.
The Danger of Interacting With Social Engineering Without Even Knowing
Social engineering is a method of attack that uses deception and impersonation to influence people into revealing information or providing access. It relies on trust and context to make people perform actions that appear harmless and legitimate at the moment.
The trick of deepfakes is that they mirror everyday communication very accurately. Attackers today have all the tools to impersonate colleagues, service providers, or internal support staff. A phone call from someone claiming to be part of the IT help desk can easily seem routine, especially when framed as a quick fix or standard check. Similar approaches can be seen in emails or messaging platforms, and the pattern is the same: urgency overrides safety.
With the various new tools available, visual deception has become very common. Employees may be directed to login pages that closely resemble internal systems and enter credentials without hesitation. Emerging techniques like AI-assisted voice or video impersonation further blur the line between legitimate requests and malicious activity, making social engineering interactions very difficult to recognize in real time.
Ignoring Security Policies and Best Practices
It’s not enough if security policies exist only as formal documentation, but are not followed consistently on the floor. Sometimes, even if access procedures are defined, employees under the pressure of time can make undocumented exceptions. Access policies, or change management rules, for example, require peer review and approval, but urgent maintenance or capacity pressures often lead to decisions that bypass those steps.
These small deviations create gaps between how systems are supposed to be protected and how they are actually handled. When policies become situational or optional, security controls lose their purpose and reliability, leaving the infrastructure exposed, even though there’s a mature security framework in place.
When Policies Leave Room for Interpretation
Policies that lack precision introduce variability into how security controls are applied across teams and shifts. When procedures don’t explicitly define how credentials should be managed on shared systems, retained login sessions, or administrative access can remain in place beyond their intended scope. Similarly, if requirements for password rotation or periodic access reviews are loosely framed or undocumented, they are more likely to be deferred during routine operations.
These conditions rarely trigger immediate alerts or audit findings. However, over time, they accumulate into systemic weaknesses that expand the attack surface and increase the likelihood of attacks.
Best Practices That Erode in Daily Operations
Security issues often emerge through slow, incremental changes. When operational pressure increases, teams might want to rely on more informal workarounds to keep everything running. Routine best practices like updates, access reviews, and configuration standards can slip down the priority list or become sloppy in their application. Individually, all of these decisions can seem reasonable at the moment; over time, however, they do add up and dilute the established safeguards, which leaves the organization exposed even without a single clearly identifiable incident.
Overlooking Access and Offboarding Control
Ignoring best practices around access management introduces the next line of risks. Employees and third-party contractors often retain privileges beyond their active role if offboarding steps are not followed through. In the lack of clear deprovisioning rules, like disabling accounts, dormant access can linger on unnoticed. These inactive accounts are not monitored closely enough to detect and identify if misuse or compromise happens.
Policy Gaps During Incident Response
The consequences of ignoring procedures become most visible when an actual cybersecurity incident occurs. When teams are forced to act quickly without clear guidance, errors start to surface. Procedures that are outdated, untested, or difficult to locate offer little support during an emergency. There’s no policy that can eliminate risks completely, however, organizations that treat procedures as living, enforceable tools are better positioned to respond effectively when an incident occurs.
A Weak Approach to Security Governance
Weak security governance often allows risks to persist unnoticed, especially when oversight from management is limited or unclear. Without clear ownership and accountability, routine tasks like applying security patches or reviewing alerts can be delayed or overlooked, leaving systems exposed. These seemingly insignificant gaps create an environment over time in which vulnerabilities are known but not actively addressed.
Training plays a very important role in closing this gap, but only when it is treated as part of governance,and not as an isolated activity. Regular, structured training helps employees develop a habit of verification and reinforces the checks and balances defined by organizational policies. To remain effective, training has to evolve in tandem with the threat landscape. Employees need ongoing exposure to emerging attack techniques and practical guidance on how to recognize and respond to them within their daily workflows. Aligned governance and training help organizations position themselves better to reduce risk driven by human factors.
Understanding the Stakes
Human error in cybersecurity is often discussed as a collection of isolated missteps, but in reality, it reflects how people operate within complex systems under constant pressure.
In data center environments, these errors rarely occur as isolated events but are influenced by interconnected processes, tight timelines, and attackers who deliberately exploit trust, familiarity, and routine behavior. Looking at it from this angle, human error doesn’t show only individual mistakes but provides insight into how risks develop across an organization over time.
Recognizing the role of human error in cybersecurity is essential for reducing future incidents, but awareness alone is not enough. Training also plays an important role, but it cannot compensate for unclear processes, weak governance, or a culture that prioritizes speed more than safety.
Data center operators have to continuously adapt their security practices and reinforce expectations through daily operations instead of treating security best practices as rigid formalities. Building a culture where employees understand how their actions influence security outcomes helps organizations respond more effectively to evolving threats and limits the conditions that allow small errors to turn into major, devastating incidents.
# # #
About the Author
Michael Zrihen is the Senior Director of Marketing & Internal Operations Manager at Volico Data Centers.
The post Human Error in Cybersecurity and the Growing Threat to Data Centers appeared first on Data Center POST.
As data centers push toward terabit-scale bandwidth, legacy copper interconnects are hitting their limit or as the industry calls it, the “copper cliff.” Traditional copper cabling, once the workhorse of short-reach connectivity, has become too thick, too inflexible, and too short to keep pace with the scale of xPU bandwidth growth in the data center. On the other hand, optical solutions will work but are saddled with the “optical penalty,” that includes power-hungry and expensive electrical and optical components, manufacturing design complexity, latency challenges and more importantly, reliability issues after deployment.
With performance, cost, and operational downsides increasing for both copper and optical interconnect, network operators are looking beyond the old interconnect paradigm and toward more scalable options to scale at the pace of the next generation AI clusters in data centers.
Enter e-Tube: the industry’s third interconnect option.
e-Tube Technology is a scalable multi-terabit interconnect platform that uses RF data transmission through a plastic dielectric waveguide. Designed to meet the coming demands of 1.6T and 3.2T bandwidth requirements, e-Tube leverages cables made from common plastic material such as low-density polyethylene (LDPE), which avoids the high-frequency loss and physical constraints inherent to copper. The result is a flexible, power-efficient, and highly reliable link that delivers the reach and performance required to scale up AI clusters in next-generation data center designs.
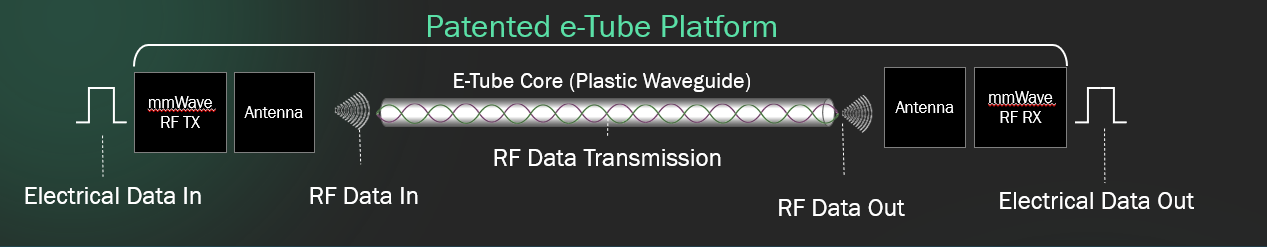
Figure 1 [Patented e-Tube Platform]
The industry is taking notice of the impact e-Tube will make, with results showing up to 10x the reach of copper while being 5x lighter and 2x thinner. Compared with optical cables, e-Tube consumes 3x less power, achieves 1,000x lower latency, and an impressive 3x less cost. Its scalable design architecture delivers consistent bandwidth for future data speeds to 448Gbps and beyond across networks, extending existing use cases and creating new applications that copper and optical interconnects cannot support.
With the impending copper cliff and optical penalty looming in the horizon, the time is now for data center operators to consider a third interconnect option. e-Tube RF transmission over a plastic dielectric delivers measurable impact with longer reach, best-in-class energy efficiency, near-zero latency, not to mention a cost-effective option. As AI workloads explode and terabit-scale fabrics become the norm, e‑Tube is posed to be a foundational cable interconnect for scaling up AI clusters for the next generation of data centers.
# # #
About the Author
Sean Park is a seasoned executive with over 25 years of experience in the semiconductors, wireless, and networking market. Throughout his career, Sean has held several leadership positions at prominent technology companies, including IDT, TeraSquare, and Marvell Semiconductor. As the CEO, CTO, and Founder at Point2 Technology, Sean was responsible for leading the company’s strategic direction and overseeing its day-to-day operations. He also served as a Director at Marvell, where he provided invaluable guidance and expertise to help the company achieve its goals. He holds a Ph.D. in Electrical Engineering from the University of Washington and also attended Seoul National University.
The post Beyond Copper and Optics: How e‑Tube Powers the Terabit Era appeared first on Data Center POST.

Compu Dynamics is once again turning a day on the course into long-term impact for the next generation of data center professionals. At its 6th Annual Charity Golf Tournament, the company raised a record-breaking $55,000 in support of Northern Virginia Community College’s (NOVA) Information and Engineering Technologies (IET) programs, pushing its cumulative contributions to the college to more than $200,000 to date.
Hosted at Bull Run Golf Club in northern Virginia, this year’s sold-out tournament drew more than 150 participants from more than 40 companies across the data center and mission-critical infrastructure ecosystem, including colocation providers, cloud and AI infrastructure companies, developers, manufacturers, and service partners. What has quickly become one of the region’s premier networking events for the data center community is equally a catalyst for local education and workforce development.
For Compu Dynamics, the tournament is about far more than friendly competition. It is one of the company’s most visible expressions of its commitment to building the future workforce that will build and power data centers.
“Our annual golf tournament has become this incredible convergence of generosity, partnership, and purpose,” said Steve Altizer, president and CEO of Compu Dynamics. “Beyond the golf and the camaraderie, we are helping equip the next generation of leaders with the skills and education they need. That’s what this is really about.”
Funds raised from the event support NOVA’s IET programs, which provide hands-on training in areas such as engineering technology and data center operations. These programs give students exposure to real-world infrastructure environments and career pathways, preparing them for high-demand roles across the digital infrastructure and critical facilities landscape.
The long-standing partnership between Compu Dynamics and NOVA demonstrates how deeply aligned industry and education can be when it comes to workforce readiness.
“We applaud Compu Dynamics for leading by example in its commitment to community colleges and the success of NOVA students,” said Kelly Persons, executive director of the NOVA Educational Foundation. “Their generosity and ongoing partnership demonstrate the power of collaboration in shaping the future workforce.”
By investing in programs that connect students directly with data center operations, engineering, and technology careers, Compu Dynamics is helping ensure that northern Virginia’s talent pipeline keeps pace with the region’s rapid growth in digital infrastructure.
Now in its sixth year, the charity tournament continues to scale in both participation and impact, underscoring how a single annual event can create sustained benefit for students, employers, and the broader community. What started as a way to bring partners together has evolved into a platform for advancing education, supporting economic mobility, and strengthening an industry that increasingly underpins every facet of the digital economy.
As data center demand accelerates – driven by cloud, AI, and the ever-expanding digital ecosystem – initiatives like Compu Dynamics’ charity tournament help ensure that opportunity in this sector is accessible to the local students who will become its future engineers, operators, and leaders.
In northern Virginia and beyond, Compu Dynamics is proving that when the industry invests in education, everyone wins.
To learn more, visit Compu Dynamics.
The post Compu Dynamics Drives Record Support for NOVA’s IET Programs at 6th Annual Charity Golf Tournament appeared first on Data Center POST.
